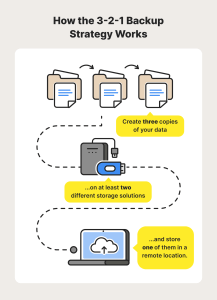
Why does your company need a Firewall? In today’s digital age, every business needs to prioritize its online security. Cyber threats are becoming more and more sophisticated and frequent, which is why having a firewall is essential. A firewall acts as a barrier between your company’s internal network and the Internet, monitoring and filtering incoming and outgoing traffic to prevent unauthorized access. Without a firewall, your company’s sensitive data and confidential information is vulnerable to cyber attacks such as ransomware, malware, viruses and phishing scams. Not only can these attacks cause significant financial damage, they can also damage your company’s reputation and erode customer trust. In this article, we’ll explore the importance of having a firewall and why it’s an investment every business should make. So let’s get started and find out why your business needs a firewall.
What is a Firewall?
A firewall is a network security device that monitors and filters incoming and outgoing network traffic based on a set of predefined security rules. It acts as a barrier between your company’s internal network and the Internet, controlling access to your network and protecting your data from unauthorized access. Firewalls can be hardware or software based and can be configured to allow or block specific types of traffic based on criteria such as port number, IP address or protocol.
Firewalls are an essential component of any security strategy, and they work by inspecting every data packet that travels between your network and the Internet. They analyze the packet header and payload to determine whether it should be allowed or blocked based on rules defined by the administrator. There are two main types of firewalls: network firewalls and host-based firewalls.
Importance of Firewall for Corporate Security
Firewalls are critical to enterprise security because they provide a first line of defense against cyberattacks. They protect your network from external threats such as hackers, viruses, and malware, as well as internal threats such as employees who may inadvertently or intentionally compromise network security. Firewalls help prevent unauthorized access to your network by blocking traffic that does not meet predefined security criteria. This could include traffic from known malicious IP addresses, traffic that violates your company’s security policies, or traffic that indicates an intrusion attempt.
In addition to protecting your network from external and internal threats, firewalls can also help prevent data breaches. Data breaches can be costly and damaging to your company’s reputation, and can result in legal and financial penalties. By implementing a firewall, you can prevent unauthorized access to sensitive data such as customer information, financial records and intellectual property. This can help ensure that your business remains compliant with industry regulations and standards.
Firewall types: Network firewall and Host-based firewall
There are two main types of firewalls: network firewalls and hose-based firewalls. Network firewalls are typically hardware devices that are installed at the perimeter of your network. They monitor and filter traffic to and from the Internet, as well as traffic between internal networks. Network firewalls can be configured to block traffic based on a variety of criteria, including IP address, port number and protocol.
Host-based firewalls, on the other hand, are software-based firewalls that are installed on individual devices such as laptops, desktops and servers. Host-based firewalls monitor and filter traffic to and from the device, providing an additional layer of protection beyond the network firewall. Host-based firewalls can be configured to block traffic based on criteria such as program, user, or file type.
How a Firewall Works: Packet Filtering and State Inspection
Firewalls work using two primary methods of filtering traffic: packet filtering and state inspection. Packet filtering examines the header of each data packet to determine whether it should be allowed or blocked based on predefined rules. Packet filtering can be effective in the block known threats, but may not be able to detect more sophisticated attacks that use encryption or tunnels.
State inspection, on the other hand, examines both the header and the content of each data packet to determine whether it should be allowed or blocked. State inspection keeps a record of the state of each connection, allowing it to detect and block suspicious traffic that could be part of an ongoing attack. State inspection can be more effective at blocking sophisticated attacks, but it can be more resource intensive than packet filtering.
Benefits of installing a Firewall
There are many benefits to installing a firewall, including:
Improved Network Security
Firewalls can help improve network security by blocking traffic that does not meet predefined security criteria. This can help prevent unauthorized access to your network and protect your data from external and internal threats.
Protection against cyber attacks
Firewalls can help protect your network against a variety of cyber attacks, including viruses, malware, and phishing scams. By blocking traffic from IP addresses and known malicious domains, firewalls can prevent these attacks from reaching your network.
Compliance with industry regulations
Firewalls can help ensure that your business remains compliant with regulations and industry standards such as HIPAA, PCI DSS, and GDPR. By preventing unauthorized access to sensitive data, firewalls can help protect your business from legal and financial penalties.
Improved productivity
Firewalls can help increase productivity by blocking access to non-work related websites and applications. By restricting access to social media, streaming sites and other distractions, firewalls can help improve employee focus and productivity.
Firewall Best Practices: Rules and Policies
To maximize the effectiveness of your firewall, it’s important to establish clear rules and policies. This includes defining what types of traffic should be allowed or blocked and establishing protocols for dealing with security incidents. Some best practices for firewall rules and policies include:
Regularly review and update the rules
Firewall rules should be reviewed and updated regularly to reflect changes in the network environment and evolving security threats.
Create a Comprehensive Security Policy
A comprehensive security policy should outline the rules and protocols for dealing with security incidents, as well as the consequences for violating security policies.
Limit access to sensitive data
Access to sensitive data must be limited to authorized personnel, and firewall rules must be configured to prevent unauthorized access.
Implement User Authentication
User authentication can help prevent unauthorized network access and ensure that users are only accessing resources they are authorized to use.
Choosing the right Firewall for your business
Choosing the right firewall for your business depends on a variety of factors, including your budget, network size and security needs. Some considerations when choosing a firewall include:
Hardware vs. Software
Hardware firewalls are typically more expensive, but offer better performance and scalability. Software firewalls are generally more affordable, but may not be as effective in handling large volumes of traffic.
Unified Threat Management (UTM)
UTM firewalls combine multiple security features such as intrusion detection and prevention, antivirus and content filtering into a single device. UTM firewalls can be a cost-effective solution for small and medium-sized businesses.
Cloud-based firewall
Cloud-based firewalls are becoming increasingly popular as more companies move their data and applications to the cloud. Cloud-based firewalls can provide scalable and flexible security for cloud-based resources.
Firewall Implementation and Management
Implementing and managing a firewall can be a complex process that requires specialized knowledge and experience. Some of the best practices for firewall implementation and management include:
Conduct a risk assessment
Before implementing a firewall, conduct a risk assessment to identify potential threats and security vulnerabilities.
Establish a Firewall Management Team
Establish a dedicated team to manage and monitor the firewall, including configuring rules and policies, monitoring network activity, and responding to security incidents.
Conduct regular audits and tests
Regular audits and testing can help identify and resolve security vulnerabilities and ensure that the firewall is working properly.
Provide Ongoing Training and Education
Provide ongoing training and education to employees to ensure they understand the importance of network security and how to use the firewall effectively.
Firewall Maintenance and Upgrades
Firewalls require regular maintenance and updates to ensure they remain effective and up to date. Some of the best practices for maintaining and updating firewalls include:
Regularly update the Firewall software
Regularly update firewall software to ensure it is protected against the latest threats and security vulnerabilities.
Conduct regular backups
Regularly back up firewall configurations and configurations to ensure that they can be quickly restored in the event of a security incident or hardware failure.
Monitor Firewall performance
Monitor firewall performance to ensure that it is operating correctly and efficiently, and make adjustments as needed.
Plan for future upgrades
Plan for future upgrades to ensure that the firewall remains a reliable and effective component of your network security strategy.
Conclusion: Protect Your Business with a Firewall
In conclusion, a firewall is an essential component of any network security strategy. It helps protect your company’s sensitive data and confidential information from external and internal threats and ensures that you remain compliant with industry regulations and standards. By implementing a firewall and following best practices for firewall rules, policies, implementation, management, maintenance and upgrades, you can help ensure your business remains safe and secure from cyber-attacks. Don’t wait until it’s too late – invest in a firewall today and protect your digital assets.